Web Application Penetration Testing
Fakir delivers the most comprehensive Penetration Testing as a Service (PtaaS) powered by Certified Hackers and AI – solving the problems of scalability and cost within an agile, DevOps-ready SaaS platform.
Request Penetration Testing
Penetration Testing as a Service that delivers more for less
-
Web application attacks increased by 52% year-over-year in 2019.
-
The average web application has 22 security vulnerabilities.
-
One out of five vulnerabilities discovered on web applications is of high severity.
-
20% of the organizations reported that their applications services were hit daily by distributed denial of services (DDoS) attacks.
-
The most common attack techniques are buffer overflow (24%), resource reduction (23%), HTTP flood (23%), Low Slow (21%), and HTTPS flood (21%).
-
Security misconfigurations are the cause of 84% of all observed vulnerabilities in web applications.
-
53% of web applications suffer from cross site scripting (XSS) vulnerabilities, and 45% have broken authentication.
-
39% of sites are vulnerable to unauthorized access, and 16% of web applications provide full system access to attackers.
Types of Penetration Testing for Web Applications
External pen testing
Attack the application from the outside. This test simulates how an outside attacker would behave when launching an attack. You can run external penetration tests to check firewalls and servers.
Internal penetration testing
Attacks from within the organization. This is usually done over a LAN connection. The goal is to identify possible vulnerabilities within the firewall and simulate an attack by a malicious insider.
In addition to the attacker’s location, there are other aspects to consider such as: B. Level of Access and Scope of Knowledge. Here are the three main types of penetration tests you can run:
Black box penetration testing
Simulate attacks launched by external actors without prior knowledge of the target system.
Gray box penetration testing
Simulate attacks launched by inside actors with user-level access to specific systems.
White box penetration testing
Simulate attacks launched by inside actors with user-level access to specific systems.
How Do You Test Web Application Security
Web application penetration testing is typically implemented in three phases: planning, deployment, and post-processing. Below is a quick checklist for your reference.
- Define the scope of the test.
- Provide the pentester with all needed information, including relevant documentation.
- Determine a success criteria for your test.
Review any available results from previous tests, if applicable. - Assess and learn as much as possible about the tested environment.
- Run the test using several different roles.
- Follow the pre-defined successes criteria and reporting procedure when discovering vulnerabilities.
- Create a clear and detailed report, explaining the measures taken, vulnerabilities detected, and the severity of each vulnerability.
- Provide recommendations for remediating the detected vulnerabilities.
- Re-test to check that the discovered vulnerabilities were properly remediated.
- Once all tests are concluded, revert all changes back to the original configuration, including proxy settings.
OWASP
Open Web Application Security Project.
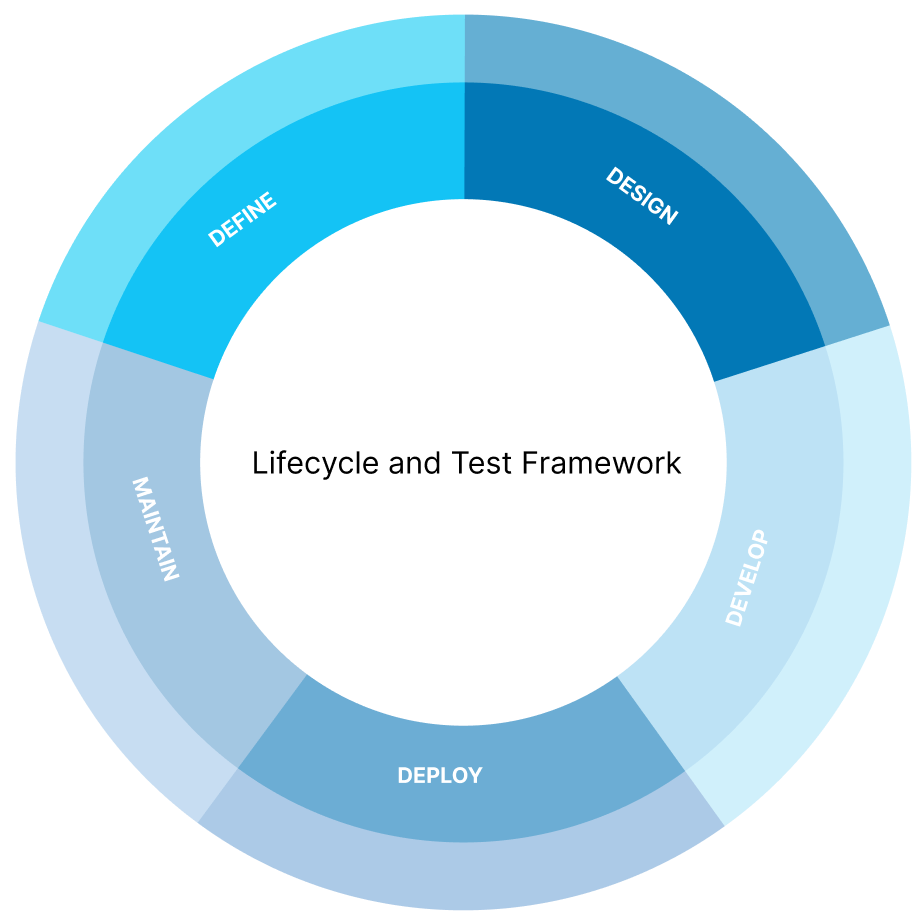
Lifecycle and Test Framework
This guide also shows how to organize audits step-by-step according to the development stage of your application. In this way, the activity runs through its entire lifecycle. So what you need to do is pre-development, definition and design phase, during development, rollout, and finally maintenance and support.
With this organizational pattern, a framework of tests is proposed to identify and detail control points upon which the corresponding tests will be applied.
Control Points and Security Tests
This procedure suggests two phases of security testing. One is the passive phase, in which the application’s behavior is monitored and all possible functions are performed. The purpose of this phase is to understand the logic of the process and identify potential vectors for attacks, vulnerabilities, or both.
In the second stage, the proposed tests are actively executed according to the vectors identified in the first stage.
The tests are grouped into 11 categories:
-
1. Information Gathering
-
2. Configuration and Deployment Management Testing
-
3. Identity Management Testing
-
4. Authentication Testing
-
5. Authorization Testing
-
6. Session Management Testing
-
7. Input Validation Testing
-
8. Error Handling
-
9. Cryptography
-
10. Business Logic Testing
-
11. Client Side Testing
Result Report
Additionally, this guide includes a section on creating audit reports. This section proposes a sample report divided into three main sections.
An executive report, which clearly and simply evaluates the results obtained by the auditor, does not go into technical details and is intended to provide a high-level overview of the impact of what was found.
- A test report describes the specifications of the actions, scope, and limitations of each test performed.
- A report of findings presenting the results of each test and recommended countermeasures to correct the observed problems.

Schedule meetings with our team
If you are looking to extend your development team, leave us your contact details so we can get back to you quickly.

